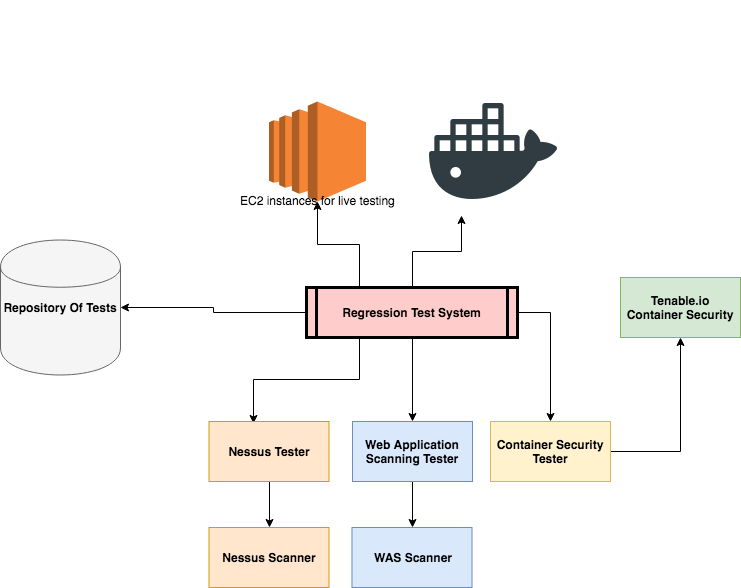
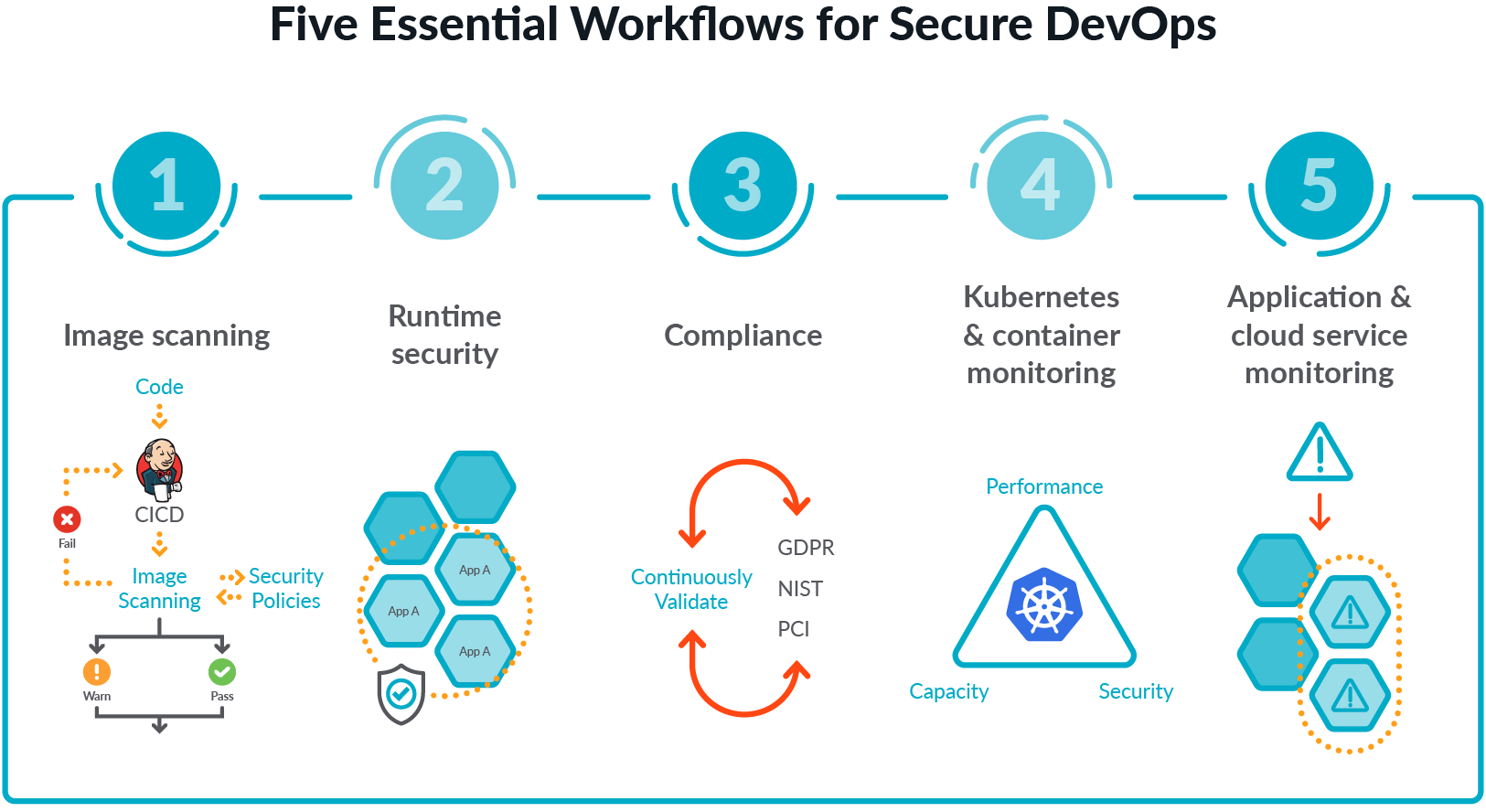
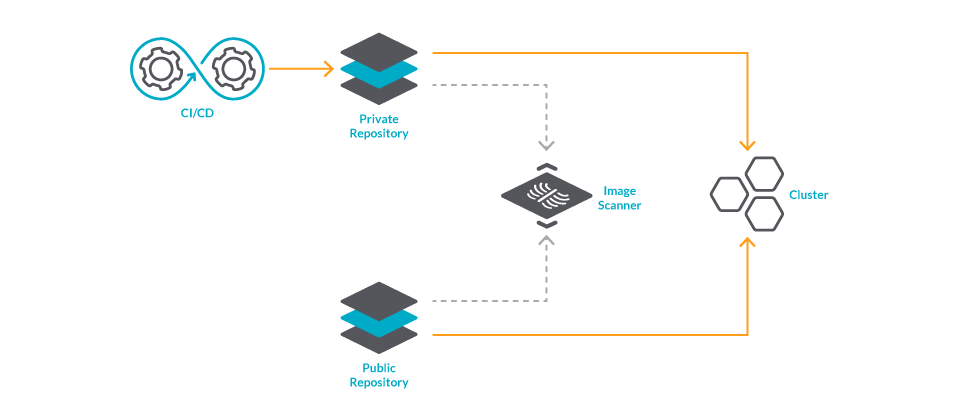
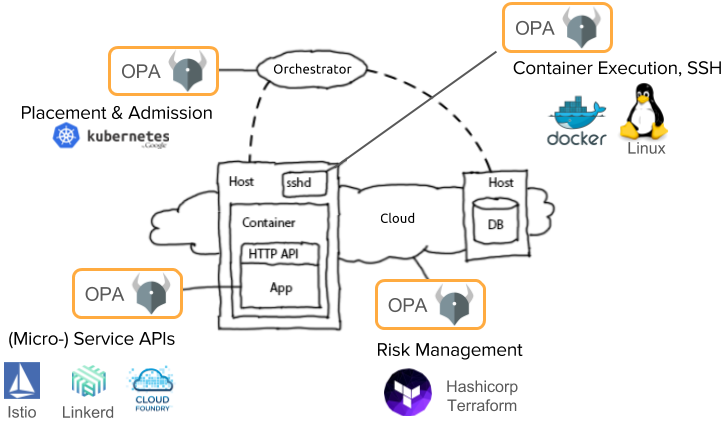
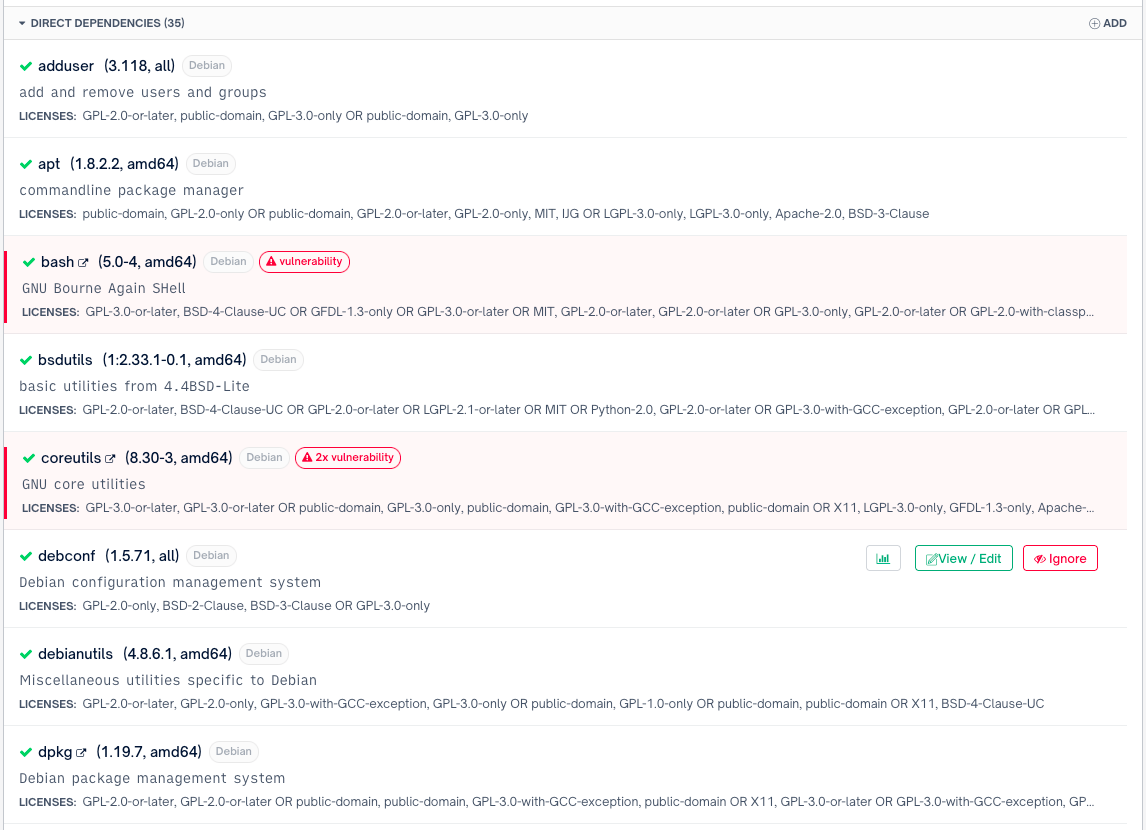
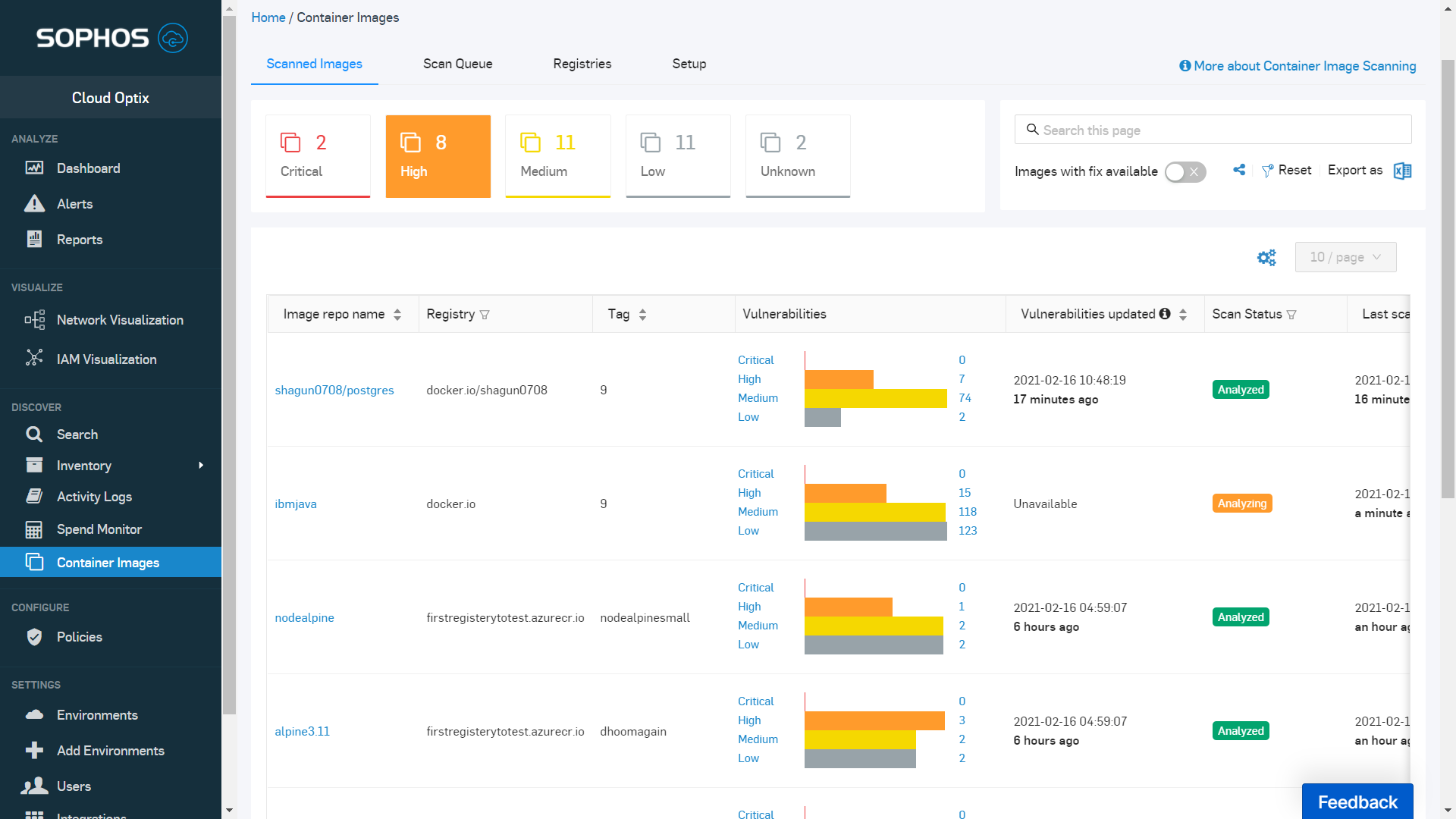
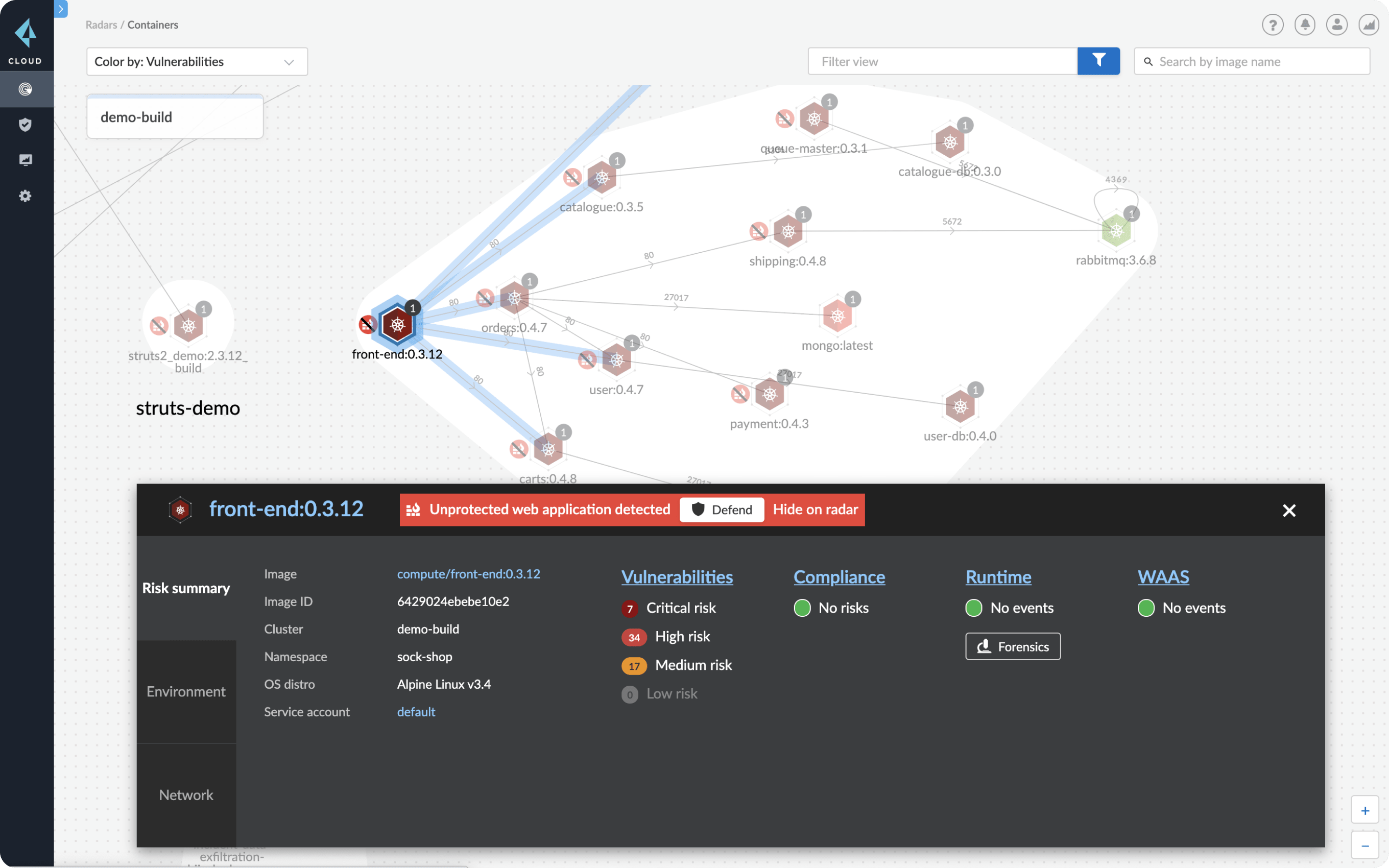
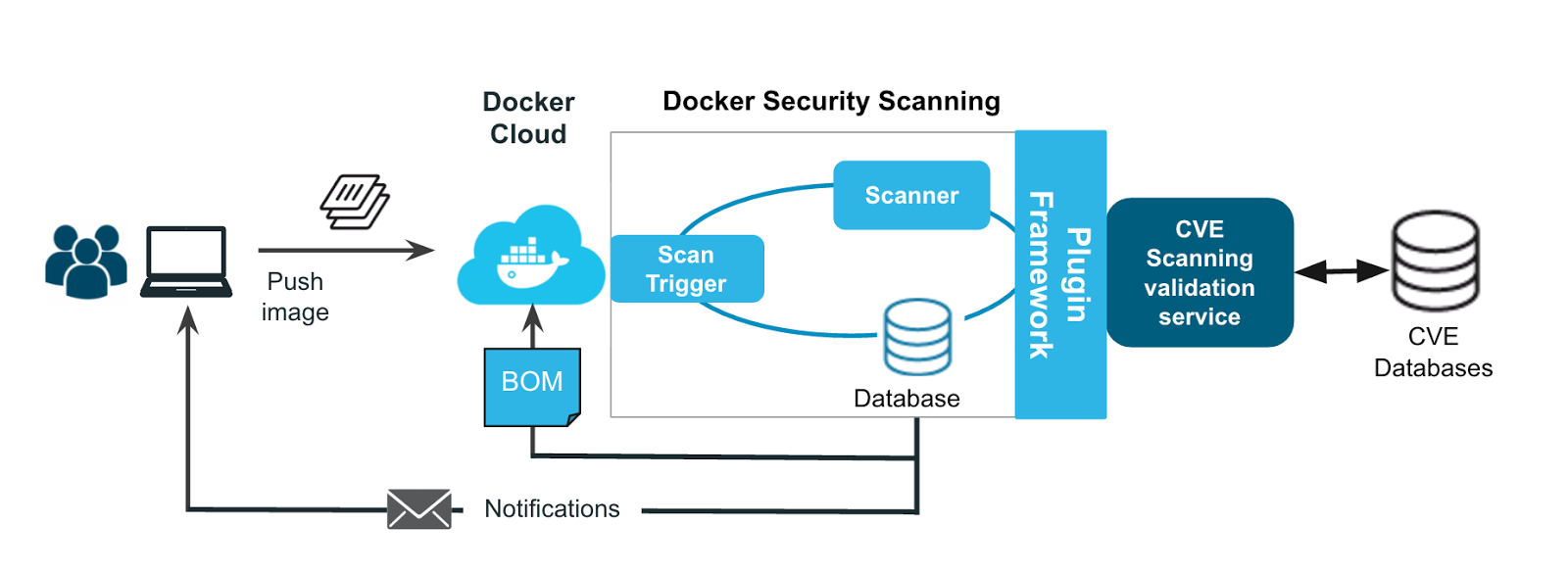
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

Adding Image Security Scanning to a CI/CD pipeline | by Larbi Youcef Mohamed Reda | alter way | Medium

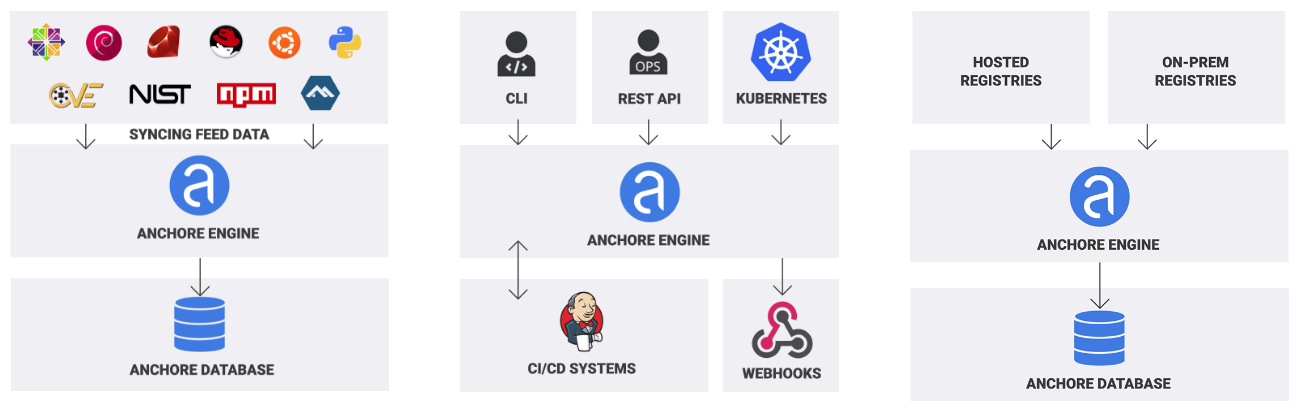
Step by step guide to integrate opensource container security scanner (Anchore engine) with CICD tool (Jenkins). | by Tanvir Ahmed | FAUN Publication